Assignment
Assignment
1. Difference between Logical DFD and Physical DFD.
Ans: Difference Between Physical and Logical DFD
|
Physical DFD |
Logical DFD |
|
it is describe h0w the process will be implemented.
|
It represent how the business operator |
|
It represent Program modules and manual procedures |
It represent the business activities.
|
|
The data stores in physical file database and manual files |
The data store represent the collection of data regardless the data store. |
.
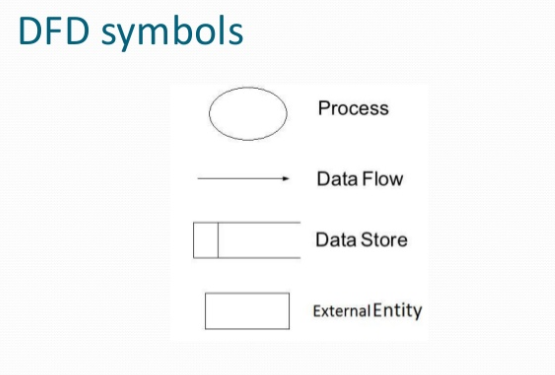
2. What is DFD? List out the Symbol used in DFD.
Ans: A data-flow diagram is a way of representing a flow of data through a process or a system (usually an information system). The DFD also provides information about the outputs and inputs of each entity and the process itself. ... Specific operations based on the data can be represented by a flowchart.
3. Explain SDLC.
Ans: SDLC is a process followed for a software project, within a software organization. It consists of a detailed plan describing how to develop, maintain, replace and alter or enhance specific software. The life cycle defines a methodology for improving the quality of software and the overall development process.
The following figure is a graphical representation of the various stages of a typical SDLC.
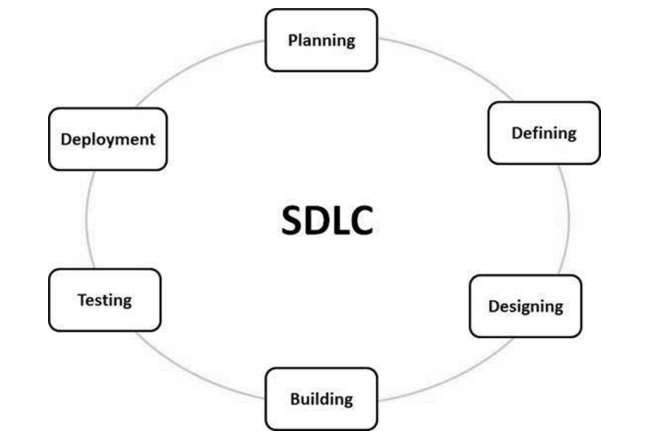
A typical Software Development Life Cycle consists of the following stages −
Stage 1: Planning and Requirement Analysis
Requirement analysis is the most important and fundamental stage in SDLC. It is performed by the senior members of the team with inputs from the customer, the sales department, market surveys and domain experts in the industry. This information is then used to plan the basic project approach and to conduct product feasibility study in the economical, operational and technical areas.
Planning for the quality assurance requirements and identification of the risks associated with the project is also done in the planning stage. The outcome of the technical feasibility study is to define the various technical approaches that can be followed to implement the project successfully with minimum risks.
Stage 2: Defining Requirements
Once the requirement analysis is done the next step is to clearly define and document the product requirements and get them approved from the customer or the market analysts. This is done through an SRS (Software Requirement Specification) document which consists of all the product requirements to be designed and developed during the project life cycle.
Stage 3: Designing the Product Architecture
SRS is the reference for product architects to come out with the best architecture for the product to be developed. Based on the requirements specified in SRS, usually more than one design approach for the product architecture is proposed and documented in a DDS - Design Document Specification.
This DDS is reviewed by all the important stakeholders and based on various parameters as risk assessment, product robustness, design modularity, budget and time constraints, the best design approach is selected for the product.
A design approach clearly defines all the architectural modules of the product along with its communication and data flow representation with the external and third party modules (if any). The internal design of all the modules of the proposed architecture should be clearly defined with the minutest of the details in DDS.
Stage 4: Building or Developing the Product
In this stage of SDLC the actual development starts and the product is built. The programming code is generated as per DDS during this stage. If the design is performed in a detailed and organized manner, code generation can be accomplished without much hassle.
Developers must follow the coding guidelines defined by their organization and programming tools like compilers, interpreters, debuggers, etc. are used to generate the code. Different high level programming languages such as C, C++, Pascal, Java and PHP are used for coding. The programming language is chosen with respect to the type of software being developed.
Stage 5: Testing the Product
This stage is usually a subset of all the stages as in the modern SDLC models, the testing activities are mostly involved in all the stages of SDLC. However, this stage refers to the testing only stage of the product where product defects are reported, tracked, fixed and retested, until the product reaches the quality standards defined in the SRS.
Stage 6: Deployment in the Market and Maintenance
Once the product is tested and ready to be deployed it is released formally in the appropriate market. Sometimes product deployment happens in stages as per the business strategy of that organization. The product may first be released in a limited segment and tested in the real business environment (UAT- User acceptance testing).
Then based on the feedback, the product may be released as it is or with suggested enhancements in the targeting market segment. After the product is released in the market, its maintenance is done for the existing customer base.
4. State any explain the rules of creating zero level DFD with example
Ans: A context diagram is a top level (also known as "Level 0") data flow diagram. It only contains one process node ("Process 0") that generalizes the function of the entire system in relationship to external entities. DFD Layers.
Rules of Level 0 DFD:
Data stores NOT shown.
They are within the system.
one process represent the entire system.
Data arrows show input and output.
5. Explain various activity involve in system design.
Ans:It produces the working system by defining the design specification that specifies exactly what the candidate system does. It is concerned with user interface design, process design, and data design.
It consists of the following steps −
Specifying the input/output media, designing the database, and specifying backup procedures.
Planning system implementation.
Devising a test and implementation plan, and specifying any new hardware and software.
Updating costs, benefits, conversion dates, and system constraints.
Architectural Design
It is also known as high level design that focuses on the design of system architecture. It describes the structure and behavior of the system. It defines the structure and relationship between various modules of system development process.
Detailed Design
It follows Architectural design and focuses on development of each module.
Conceptual Data Modeling
It is representation of organizational data which includes all the major entities and relationship. System analysts develop a conceptual data model for the current system that supports the scope and requirement for the proposed system.
The main aim of conceptual data modeling is to capture as much meaning of data as possible. Most organization today use conceptual data modeling using E-R model which uses special notation to represent as much meaning about data as possible.
Entity Relationship Model
It is a technique used in database design that helps describe the relationship between various entities of an organization.
Terms used in E-R model
ENTITY − It specifies distinct real world items in an application. For example: vendor, item, student, course, teachers, etc.
RELATIONSHIP − They are the meaningful dependencies between entities. For example, vendor supplies items, teacher teaches courses, then supplies and course are relationship.
ATTRIBUTES − It specifies the properties of relationships. For example, vendor code, student name. Symbols used in E-R model and their respective meanings −
The following table shows the symbols used in E-R model and their significance −
| Symbol | Meaning |
|---|---|
 | Entity |
 | Weak Entity |
 | Relationship |
 | Identity Relationship |
 | Attributes |
 | Key Attributes |
 | Multivalued |
 | Composite Attribute |
 | Derived Attributes |
 | Total Participation of E2 in R |
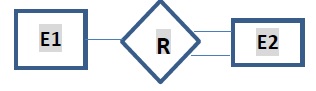 | Cardinality Ratio 1:N for E1:E2 in R |
Three types of relationships can exist between two sets of data: one-to-one, one-to-many, and many-to-many.
File Organization
It describes how records are stored within a file.
There are four file organization methods −
Serial − Records are stored in chronological order (in order as they are input or occur). Examples − Recording of telephone charges, ATM transactions, Telephone queues.
Sequential − Records are stored in order based on a key field which contains a value that uniquely identifies a record. Examples − Phone directories.
Direct (relative) − Each record is stored based on a physical address or location on the device. Address is calculated from the value stored in the record’s key field. Randomizing routine or hashing algorithm does the conversion.
Indexed − Records can be processed both sequentially and non-sequentially using indexes.
6. Explain role of system analyst in system development process.
Ans
Role of System Analyst
The system analyst is a person who is thoroughly aware of the system and guides the system development project by giving proper directions. He is an expert having technical and interpersonal skills to carry out development tasks required at each phase.
He pursues to match the objectives of information system with the organization goal.
Main Roles
Defining and understanding the requirement of user through various Fact finding techniques.
Prioritizing the requirements by obtaining user consensus.
Gathering the facts or information and acquires the opinions of users.
Maintains analysis and evaluation to arrive at appropriate system which is more user friendly.
Suggests many flexible alternative solutions, pick the best solution, and quantify cost and benefits.
Draw certain specifications which are easily understood by users and programmer in precise and detailed form.
Implemented the logical design of system which must be modular.
Plan the periodicity for evaluation after it has been used for some time, and modify the system as needed.
Attributes of a Systems Analyst
The following figure shows the attributes a systems analyst should possess −
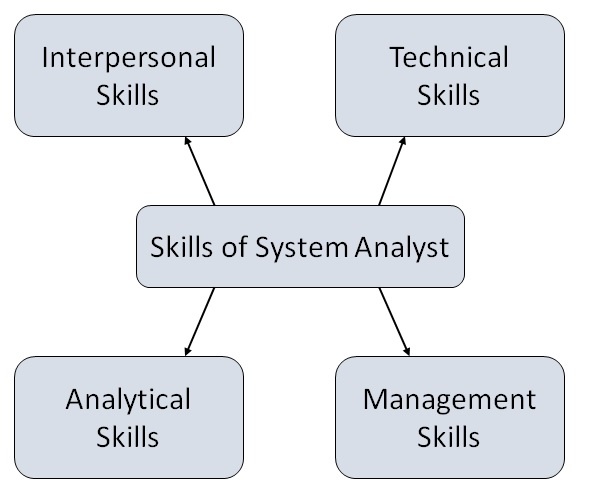
Interpersonal Skills
- Interface with users and programmer.
- Facilitate groups and lead smaller teams.
- Managing expectations.
- Good understanding, communication, selling and teaching abilities.
- Motivator having the confidence to solve queries.
Analytical Skills
- System study and organizational knowledge
- Problem identification, problem analysis, and problem solving
- Sound commonsense
- Ability to access trade-off
- Curiosity to learn about new organization
Management Skills
- Understand users jargon and practices.
- Resource & project management.
- Change & risk management.
- Understand the management functions thoroughly.
Technical Skills
- Knowledge of computers and software.
- Keep abreast of modern development.
- Know of system design tools.
- Breadth knowledge about new technologies.
7. List any two common errors that are made while data flow diagrams
Ans:
Several common errors made when drawing data flow diagrams are as follows:
- Forgetting
to include a data flow or pointing an arrow in the wrong direction. An
example is a drawn process showing all its data flow as either input or
output. Each process transforms data and must receive input and produce
output. This type of error usually occurs when the analyst has forgotten
to include a data flow or has placed an arrow pointing in the wrong
direction. Process 1 in the figure illustrated below contains only input
because the GROSS PAY arrow is pointing in the wrong direction. This
error also affects process 2, CALCULATE WITHHOLDING AMOUNT, which is in
addition missing a data flow representing input for the withholding
rates and the number of dependents.
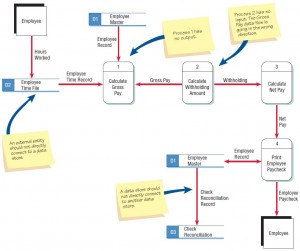 Typical errors that can occur in a data flow diagram (payroll example).
Typical errors that can occur in a data flow diagram (payroll example). - Connecting data stores and external entities directly to each other. Data stores and entities may not be connected to each other; data stores and external entities must connect only with a process. A file does not interface with another file without the help of a program or a person moving the data, so EMPLOYEE MASTER cannot directly produce the CHECK RECONCILIATION file. External entities do not directly work with files. For example, you would not want a customer rummaging around in the customer master file. Thus, the EMPLOYEE does not create the EMPLOYEE TIME FILE. Two external entities directly connected indicate that they wish to communicate with each other. This connection is not included on the data flow diagram unless the system is facilitating the communication. Producing a report is an instance of this sort of communication. A process must still be interposed between the entities to produce the report, however.
- Incorrectly labeling processes or data flow. Inspect the data flow diagram to ensure that each object or data flow is properly labeled. A process should indicate the system name or use the verb-adjective-noun format. Each data flow should be described with a noun.
- Including more than nine processes on a data flow diagram. Having too many processes creates a cluttered diagram that is confusing to read and hinders rather than enhances communication. If more than nine processes are involved in a system, group some of the processes that work together into a subsystem and place them in a child diagram.
- Omitting data flow. Examine your diagram for linear flow, that is, data flow in which each process has only one input and one output. Except in the case of very detailed child data flow diagrams, linear data flow is somewhat rare. Its presence usually indicates that the diagram has missing data flow. For instance, the process CALCULATE WITHHOLDING AMOUNT needs the number of dependents that an employee has and the WITHHOLDING RATES as input. In addition, NET PAY cannot be calculated solely from the WITHHOLDING, and the EMPLOYEE PAYCHECK cannot be created from the NET PAY alone; it also needs to include an EMPLOYEE NAME, as well as the current and year-to-date payroll and WITHHOLDING AMOUNT figures.
- Creating
unbalanced decomposition (or explosion) in child diagrams. Each child
diagram should have the same input and output data flow as the parent
process. An exception to this rule is minor output, such as error lines,
which are included only on the child diagram. The data flow diagram in
shown in the figure below is correctly drawn. Note that although the
data flow is not linear, you can clearly follow a path directly from the
source entity to the destination entity.
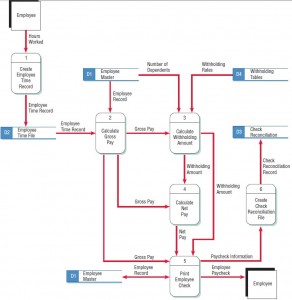 The correct data flow diagram for the
The correct data flow diagram for the
8. What is the purpose of system testing? What should be the output of the system testing?
Ans:
SYSTEM TESTING is a level of software testing where a complete and integrated software is tested. The purpose of this test is to evaluate the system’s compliance with the specified requirements.

Definition by ISTQB
- system testing: The process of testing an integrated system to verify that it meets specified requirements.
Analogy
During the process of manufacturing a ballpoint pen, the cap, the body, the tail, the ink cartridge and the ballpoint are produced separately and unit tested separately. When two or more units are ready, they are assembled and Integration Testing is performed. When the complete pen is integrated, System Testing is performed.
Method
Usually, Black Box Testing method is used.
Tasks
- System Test Plan
- Prepare
- Review
- Rework
- Baseline
- System Test Cases
- Prepare
- Review
- Rework
- Baseline
- System Test
- Perform
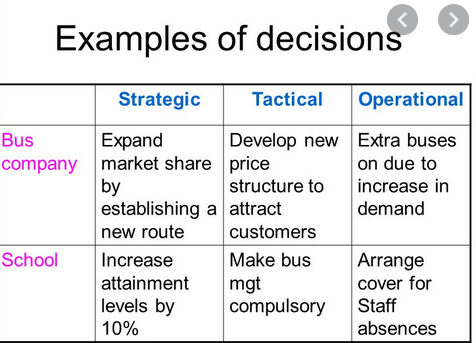
9. Give one example each for strategic, tactical and operational decisions.
Ans:
Strategic planning is an organization’s process of defining its strategy, or direction, and making decisions on allocating its resources to pursue this strategy. Generally, strategic planning deals, on the whole business, rather than just an isolated unit, with at least one of following three key questions:
- “What do we do?”
- “For whom do we do it?”
- “How do we excel?”
For example
the first and third questions are those that motivate an acquisition. Acquisitions are thus strategic choices. Typically strategic choices look at 3 to 5 years, although some extend their vision to 20 years (long term). Because of the time horizon and the nature of the questions dealt, mishaps potentially occurring during the execution of a strategic plan are afflicted by significant uncertainties and may lie very remotely out of the control of management (war, geopolitical shocks, etc.). Those mishaps, in conjunction to their potential consequences are called “strategic risks”. Untapped opportunities can also be seen as strategic risks, but in this post we will not analyze those upward-risks aspects.
Tactical planning is short range planning emphasizing the current operations of various parts of the organization. Short Range is generally defined as a period of time extending about one year or less in the future. Managers use tactical planning to outline what the various parts of the organization must do for the organization to be successful at some point one year or less into the future. Tactical plans are usually developed in the areas of production, marketing, personnel, finance and plant facilities. Because of the time horizon and the nature of the questions dealt, mishaps potentially occurring during the execution of a tactical plan should be covered by moderate uncertainties and may lie closer to the control of management (next year shipping prices, energy consumption, but not a catastrophic black-out, etc.) than strategic ones. Those mishaps, in conjunction to their potential consequences are called “tactical risks”.
Operational planning is the process of linking
strategic goals and objectives to tactical goals and objectives. It
describes milestones, conditions for success and explains how, or what
portion of, a strategic plan will be put into operation during a given
operational period.
An operational plan addresses four questions:
10. How cost-benefit analysis plays an important role in SDLC?
Ans:
POWERFUL COST-BENEFIT ANALYSIS FOR SOFTWARE DEVELOPMENT
Today’s
marketplace remains captivated by key catchphrases or buzzwords that
focus on different aspects of increasing efficiency or results. While
some such phrases may be passing fads, others are the cornerstones of
successful business practices and the companies that adopt them are the
ones that will stand the test of time.
Cost-benefit analysis is one such concept that should be considered a critical component of the software development process. With
an average failure rate of 20%, software projects are at a high risk
for costing more money than they generate. Performing a thorough
analysis of a project’s costs and expected benefits or outcomes is the
only way to identify whether or not a given project will be
profitable—and therefore viable—for your company.
BUSINESS BENEFITS OF COST-BENEFIT ANALYSIS
A focus on quality products is a great asset to any business. However, without the ability to generate profits, the quality of your product offering has little value. If you cannot afford to stay in business because your development time and costs outweigh the amount of revenue earned from sales, your attention to detail and strong commitment to user needs will be lost. There are three primary benefits that smart businesses can enjoy from a cost-benefit analysis:
- Loss prevention
When you can clearly see the costs that go into your software program and balance those with the sales profits, you will be able to prevent pouring more money into a product than you get out of it. - Increased profits
Preventing a loss is important but it is in the generation of profits that your business can really succeed. A cost-benefit analysis can help to illustrate ways that your company can increase software sales, revenue and ultimately profits. - Improved decision making
Every part of the software development process offers opportunities to streamline operations, reduce costs, or improve performance if the right information is made available. Having data readily accessible can help management and development teams make the right decisions at the right times.
Implementing a comprehensive system of cost-benefit analysis will help you determine whether or not your project can be successful. It can also help you identify changes that can be made in order to ensure the success of your work.
11. What is the drawback of DFD
Ans:
As the name suggests, a Data Flow Diagram represents how data is passed through a system. To do this, it provides information about the input, output, and the processes related to the system. In simple words, it depicts the flow between different entities in a system and how data is processed. Mostly, it looks like a flowchart and helps us work on database management and system analysis.
12. List characteristics of a good interface.
Ans:
There is a lot of information out there about various interface design techniques and patterns you can use when crafting your user interfaces and websites, solutions to common problems and general usability recommendations. Following guidelines from experts will likely lead you towards creating a good user interface – but what exactly is a good interface? What are the characteristics of an effective user interface?
Here are 8 things I consider a good user interface needs to be:
13. Explain different ways in which an analyst gathers requirement from the customer.
Ans:
Here are the few guidelines that can help the Business Analyst to capture complete, correct requirements:
1) Pick the Interview Groups wisely. Business Analyst should consider
various factors while group selections: Technical Maturity, Business
Process Knowledge, Specialization, Interest, Departments, Organization
sections, and Time Availability.
2) Before starting the Requirement
Gathering, it’s good to summarize/introduce the project and associated
purpose, to avoid misconceptions of teams involved in this phase.
3) Business Analyst should follow up each question with a set of clarifying questions to dig it further.
4) Always take collaborative approach while gather the requirements.
5) Keep the questionnaire descriptive and simple to understand.
6) Initially, ask the Vendors for the list of requirements with
associated details. This will help Business Analyst to frame questions.
7) Carryout the Polls, so that users rank their needs, and have a place to provide feedback.
14. What is MIS? What are different components of MIS? Explain different categories of information required to serve the needs of different levels of management in an organization.
Ans:
Data refers to raw basic facts i.e. price of a product, the number of products purchased, etc. that haven't yet been
For example, a price of $6 and a quantity of 10 do not convey any meaning to a customer at a point of sale till. Information should be processed data that conveys meaning to the recipient.
For example, multiplying $6 by 10 gives us $60, which is the total bill that the customer should pay.
Good information should be timely and available when it is needed.
The following are the characteristics of good information.
- Accurate – information must be free from errors and mistakes. This is achieved by following strict set standards for processing data into information. For example, adding $6 + 10 would give us inaccurate information. Accurate information for our example is multiplying $6 by 10.
- Complete – all the information needed to make a good decision must be available. Nothing should be missing. If TAX is an application to the computation of the total amount that the customer should pay then, it should be included as well. Leaving it out can mislead the customer to think they should pay $60 only when in actual fact, they must pay tax as well.
- Cost Effective – the cost of obtaining information must not exceed the benefit of the information in monetary terms.
- User-focused – the information must be presented in such a way that it should address the information requirements of the target user. For example, operational managers required very detailed information, and this should be considered when presenting information to operational managers. The same information would not be appropriate for senior managers because they would have to process it again. To them, it would be data and not information.
- Relevant – the information must be relevant to the recipient. The information must be directly related to the problem that the intended recipient is facing. If the ICT department wants to buy a new server, information that talks about a 35% discount on laptops would not be relevant in such a scenario.
- Authoritative – the information must come from a reliable source. Let's say you have a bank account and you would like to transfer money to another bank account that uses a different currency from yours. Using the exchange rate from a bureau de change would not be considered authoritative compared to getting the exchange rate directly from your bank.
- Timely – information should be available when it is needed. Let's say your company wants to merge with another company. Information that evaluates the other company that you want to merge with must be provided before the merger, and you must have sufficient time to verify the information.
Competitive advantage of information and MIS
Competitive advantage is a position that makes a business more profitable than its competitors. For example, producing products at a lower cost than your competitors makes you more profitable.
Information systems have the capacity to help an organization into such a position. They do so in the following ways
Operational excellence – operational excellence seeks to improve the operations of the business. Let's take an example of a retail store. A retail store can use information systems to automatically place an order with a supplier once the inventory level reaches the re-order limit. This ensures that the retail store never runs out of inventory and customers can always count on it to find what they need.
New business models, products, and services – let's continue with the example of a retail store. The retail store can develop a web based order system or smartphone application that clients can use to buy items from the comfort of their homes or wherever they are. The order system can be linked to a delivery business and have support for online payments. This is a new business model compared to customers walking in to make purchases vs doing it from web based or smartphone apps.
Improved supplier and customer relations – historical data is used to understand the needs of the customers and suppliers. This data is then used to create services and products that address the needs. This leads to long-term relationships with customers and business which puts an organization in a more profitable position.
Improved decision making – information is critical when making decisions. Information systems if designed and operated efficiently, output information that has all the characteristic of good information described in the above section. This enables an organization to make decisions that will profit the organizations.
Components of MIS and their relationship
A management information system is made up of five major components namely people, business processes, data, hardware, and software. All of these components must work together to achieve business objects.
People – these are the users who use the information system to record the day to day business transactions. The users are usually qualified professionals such as accountants, human resource managers, etc. The ICT department usually has the support staff who ensure that the system is running properly.
Business Procedures – these are agreed upon best practices that guide the users and all other components on how to work efficiently. Business procedures are developed by the people i.e. users, consultants, etc.
Data – the recorded day to day business transactions. For a bank, data is collected from activities such as deposits, withdrawals, etc.
Hardware – hardware is made up of the computers, printers, networking devices, etc. The hardware provides the computing power for processing data. It also provides networking and printing capabilities. The hardware speeds up the processing of data into information.
Software – these are programs that run on the hardware. The software is broken down into two major categories namely system software and applications software. System software refers to the operating system i.e. Windows, Mac OS, and Ubuntu, etc. Applications software refers to specialized software for accomplishing business tasks such as a Payroll program, banking system, point of sale system, etc.
15. What is DSS? Explain application of DSS in today’s world? What is the difference between MIS and DSS?
Ans:
MIS
MIS, Management Information System, is a computer based program to assist users to make decisions based on information present in the system.
DSS
DSS, Decision Support System, is also to help making decisions. It uses communication technologies, data, documents to identify problems and to finalize decisions.
Following are the important differences between MIS and DSS.
| Sr. No. | Key | MIS | DSS |
|---|---|---|---|
| 1 | Primary Task | MIS identifies the information required. | DSS identifies the tools to be used in decision process. |
| 2 | Focus | Focus is on efficiency. | Focus is on effectiveness. |
| 3 | Database | Corporate Databases are used. | Special Database needed. |
| 4 | Data | Focus is on data storage. | Focus is on data manipulation. |
| 5 | Dependency | Dependent on computer. | Dependent on management juridiction. |
| 6 | Usage | MIS is used to in control process. | DSS is used in planning, staffing and decision making. |
| 7 | Users | MIS is used by middle level, low level users and senior executives in some cases. | DSS is used by analysts, professionals and managers. |
| 8 | Focus | Focus is on information processing. | Focus is on decision making, support and analysis. |
16. What is structured analysis? Name a tool that carried out structured analysis? Explain the tool.
Ans:
Structured Analysis is a development method that allows the analyst to understand the system and its activities in a logical way.
It is a systematic approach, which uses graphical tools that analyze and refine the objectives of an existing system and develop a new system specification which can be easily understandable by user.
It has following attributes −
It is graphic which specifies the presentation of application.
It divides the processes so that it gives a clear picture of system flow.
It is logical rather than physical i.e., the elements of system do not depend on vendor or hardware.
It is an approach that works from high-level overviews to lower-level details.
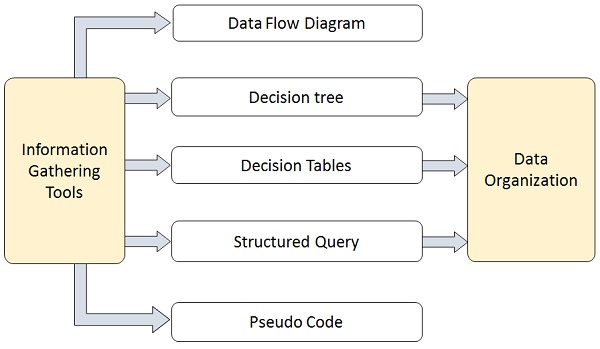
Structured Analysis Tools
During Structured Analysis, various tools and techniques are used for system development. They are −
- Data Flow Diagrams
- Data Dictionary
- Decision Trees
- Decision Tables
- Structured English
- Pseudocode
17. Differentiate black box testing and white box testing. Can one be used in place of other? Give reasons.
Ans:
What is Black Box testing?
In Black-box testing, a tester doesn't have any information about the internal working of the software system. Black box testing is a high level of testing that focuses on the behavior of the software. It involves testing from an external or end-user perspective. Black box testing can be applied to virtually every level of software testing: unit, integration, system, and acceptance.
What is White Box testing?
White-box testing is a testing technique which checks the internal functioning of the system. In this method, testing is based on coverage of code statements, branches, paths or conditions. White-Box testing is considered as low-level testing. It is also called glass box, transparent box, clear box or code base testing. The white-box Testing method assumes that the path of the logic in a unit or program is known.
KEY DIFFERENCE
- In Black Box, testing is done without the knowledge of the internal structure of program or application whereas in White Box, testing is done with knowledge of the internal structure of program.
- Black Box test doesn’t require programming knowledge whereas the White Box test requires programming knowledge.
- Black Box testing has the main goal to test the behavior of the software whereas White Box testing has the main goal to test the internal operation of the system.
- Black Box testing is focused on external or end-user perspective whereas White Box testing is focused on code structure, conditions, paths and branches.
- Black Box test provides low granularity reports whereas the White Box test provides high granularity reports.
- Black Box testing is a not time-consuming process whereas White Box testing is a time-consuming process.
Difference between Black Box testing and White Box testing
| Parameter | Black Box testing | White Box testing |
|---|---|---|
| Definition | It is a testing approach which is used to test the software without the knowledge of the internal structure of program or application. | It is a testing approach in which internal structure is known to the tester. |
| Alias | It also knowns as data-driven, box testing, data-, and functional testing. | It is also called structural testing, clear box testing, code-based testing, or glass box testing. |
| Base of Testing | Testing is based on external expectations; internal behavior of the application is unknown. | Internal working is known, and the tester can test accordingly. |
| Usage | This type of testing is ideal for higher levels of testing like System Testing, Acceptance testing. | Testing is best suited for a lower level of testing like Unit Testing, Integration testing. |
| Programming knowledge | Programming knowledge is not needed to perform Black Box testing. | Programming knowledge is required to perform White Box testing. |
| Implementation knowledge | Implementation knowledge is not requiring doing Black Box testing. | Complete understanding needs to implement WhiteBox testing. |
| Automation | Test and programmer are dependent on each other, so it is tough to automate. | White Box testing is easy to automate. |
| Objective | The main objective of this testing is to check what functionality of the system under test. | The main objective of White Box testing is done to check the quality of the code. |
| Basis for test cases | Testing can start after preparing requirement specification document. | Testing can start after preparing for Detail design document. |
| Tested by | Performed by the end user, developer, and tester. | Usually done by tester and developers. |
| Granularity | Granularity is low. | Granularity is high. |
| Testing method | It is based on trial and error method. | Data domain and internal boundaries can be tested. |
| Time | It is less exhaustive and time-consuming. | Exhaustive and time-consuming method. |
| Algorithm test | Not the best method for algorithm testing. | Best suited for algorithm testing. |
| Code Access | Code access is not required for Black Box Testing. | White box testing requires code access. Thereby, the code could be stolen if testing is outsourced. |
| Benefit | Well suited and efficient for large code segments. | It allows removing the extra lines of code, which can bring in hidden defects. |
| Skill level | Low skilled testers can test the application with no knowledge of the implementation of programming language or operating system. | Need an expert tester with vast experience to perform white box testing. |
| Techniques | Equivalence partitioning is Black box testing technique is used for Blackbox testing. Equivalence partitioning divides input values into valid and invalid partitions and selecting corresponding values from each partition of the test data. Boundary value analysis checks boundaries for input values. | Statement Coverage, Branch coverage, and Path coverage are White Box testing technique. Statement Coverage validates whether every line of the code is executed at least once. Branch coverage validates whether each branch is executed at least once Path coverage method tests all the paths of the program. |
| Drawbacks | Update to automation test script is essential if you to modify application frequently. | Automated test cases can become useless if the code base is rapidly changing. |
18. How do tangible costs differ from direct costs?
Ans:
Direct Costs
Direct costs are costs directly tied to a product or service that a company produces. Direct costs can be easily traced to their cost objects. Cost objects can include goods, services, departments, or projects.
Direct costs include:
- Direct labor
- Direct materials
- Manufacturing supplies
- Wages tied to production
Direct costs can also be fixed costs, such as rent payments that are directly tied to a production facility. Also, salaries of mangers or supervisors might also be included in direct costs, particularly if they're tied to a specific project. Typically, direct fixed costs don't vary, meaning they don't fluctuate with the number of units produced.
Variable Costs
Variable costs are costs that vary as production of a product or service increases or decreases. Unlike direct costs, variable costs depend on the company’s production volume. When a company’s production output level increases, variable costs increase. Conversely, variable costs fall as the production output level decreases.
For example, the packaging costs associated with a product would be a variable cost since the packaging costs would increase as sales increased. The raw materials used to make the product would also be variable costs since the cost of materials would rise and fall depending on sales volume of the product. The raw materials would also be a variable cost.
In addition to direct materials, other examples of variable costs include
- Although labor is typically a fixed cost, some labor is variable. Piecework labor, which is the labor cost that's tied to the number of pieces produced or worked on by each employee.
- Supplies for the factory or machinery might be variable, including oil for the machines or parts tied to production. These supplies are different than raw materials.
- Billable hours for employees who are paid hourly, such as those needed for the production facility or consulting can be variable costs.
- Commissions for the sales staff are often tied to production or the number of units sold. As they sell more goods, sales commissions increase as a variable cost.
- Merchant credit card fees, if a company accepts credit cards for payment, are typically charged to businesses as a percentage of their sales. However, any fixed fees for the service or the machine are considered fixed costs.
- Shipping or delivery costs are often variable costs directly tied to the volume of sales and production.
However, variable costs do not need to be directly related to the product. In other words, a variable cost can be an indirect cost.
19. What are functional requirement and non-functional requirement?
Ans:
While functional requirements define what the system does or must not do, non-functional requirements specify how the system should do it. Non-functional requirements do not affect the basic functionality of the system (hence the name, non-functional requirements). Even if the non-functional requirements are not met, the system will still perform its basic purpose.
If a system will still perform without meeting the non-functional requirements, why are they important? The answer is usability. Non-functional requirements define system behaviour, features, and general characteristics that affect the user experience. How well non-functional requirements are defined and executed determines how easy the system is to use, and is used to judge system performance. Non-functional requirements are product properties and focus on user expectations.
There are more examples below, but for now, think about a functional requirement that the system loads a webpage after someone clicks on a button. There should be a related non-functional requirement specifying how fast the webpage must load. Without it, the user experience and perception of quality are at risk if they are forced to wait too long, even though the functional requirement is fully met.

20. Explain Output Format types: Tabular format, Graphical format, Detailed Reports and Summary Reports with proper diagram and format.
ans:
| FORMAT | DESCRIPTION |
|---|---|
| Tabular | Tabular reports are the simplest and fastest way to look at data. Similar to a spreadsheet, they consist simply of an ordered set of fields in columns, with each matching record listed in a row. Tabular reports are best for creating lists of records or a list with a single grand total. They can't be used to create groups of data or charts, and can't be used in dashboards unless rows are limited. Examples include contact mailing lists and activity reports. |
| Summary | Summary reports are similar to tabular reports, but also allow users to group rows of data, view subtotals, and create charts. They can be used as the source report for dashboard components. Use this type for a report to show subtotals based on the value of a particular field or when you want to create a hierarchical list, such as all opportunities for your team, subtotaled by Stage and Owner. Summary reports with no groupings show as tabular reports on the report run page. |
| Matrix | Matrix reports are similar to summary reports but allow you to group and summarize data by both rows and columns. They can be used as the source report for dashboard components. Use this type for comparing related totals, especially if you have large amounts of data to summarize and you need to compare values in several different fields, or you want to look at data by date and by product, person, or geography. Matrix reports without at least one row and one column grouping show as summary reports on the report run page. |
| Joined | Joined reports let you create multiple report blocks that provide different views of your data. Each block acts like a “sub-report,” with its own fields, columns, sorting, and filtering. A joined report can even contain data from different report types. Joined reports are available only in Enterprise, Performance, Unlimited, and Developer Editions.
|
21. What is in your opinion the most difficult job for system analyst?
Ans:
A systems analyst, also known as business technology analyst, is an information technology (IT) professional who specializes in analyzing, designing and implementing information systems. Systems analysts assess the suitability of information systems in terms of their intended outcomes and liaise with end users, software vendors and programmers in order to achieve these outcomes.[1] A systems analyst is a person who uses analysis and design techniques to solve business problems using information technology. Systems analysts may serve as change agents who identify the organizational improvements needed, design systems to implement those changes, and train and motivate others to use the systems.[2]
Although they may be familiar with a variety of programming languages, operating systems, and computer hardware platforms, they do not normally involve themselves in the actual hardware or software development. They may be responsible for developing cost analysis, design considerations, staff impact amelioration, and implementation timelines.
A systems analyst is typically confined to an assigned or given system and will often work in conjunction with a business analyst. These roles, although having some overlap, are not the same. A business analyst will evaluate the business need and identify the appropriate solution and, to some degree, design a solution without diving too deep into its technical components, relying instead on a systems analyst to do so. A systems analyst will often evaluate and modify code as well as review scripting.
Some dedicated professionals possess practical knowledge in both areas (business and systems analysis) and manage to successfully combine both of these occupations, effectively blurring the line between business analyst and systems analyst.
22. Explain Open and Close System with example.
Ans:
Open System
An open system is a system that freely exchanges energy and matter with its surroundings. For instance, when you are boiling soup in an open saucepan on a stove, energy and matter are being transferred to the surroundings through steam.
Closed System
Putting a lid on the saucepan makes the saucepan a closed system. A closed system is a system that exchanges only energy with its surroundings, not matter. By putting a lid on the saucepan, matter can no longer transfer because the lid prevents matter from entering the saucepan and leaving the saucepan.
23. Explain Information Gathering Technique- Questionnaires?
Ans :
Managing information involves gathering and distributing necessary information and assimilating them on the project management activities and processes. The information gathering techniques are repeated processes that are used to create and organize data across different kinds of sources. There are four types of information gathering techniques as follows:
- Brainstorming: This method is used to get a list of all project lists. All ideas are generated with the help of a facilitator through an open discussion and mass interviewing techniques. Commonly, the brainstorming technique can be done during a scheduled meeting with peers, individual brainstorming, or even at an informal meeting.
- Delphi technique: This technique in project management requires the presence of a facilitator that gives out questionnaires to solicit different ideas. The responses are summarized and recirculated to the participants.
- Root cause analysis: One of the information gathering techniques is the root cause analysis. It is used in identifying problems and its underlying causes thus developing a preventive action.
- Interviewing: Stakeholders, participants, and experts are interviewed to identify risks.
24. What are The Types of Feasibility?
Ans :
- Technical Feasibility. This assessment focuses on the technical resources available to the organization. ...
- Economic Feasibility. ...
- Legal Feasibility. ...
- Operational Feasibility. ...
- Scheduling Feasibility.
25. What are The Types of Systems?
Ans:
- An open system can exchange both energy and matter with its surroundings. ...
- A closed system, on the other hand, can exchange only energy with its surroundings, not matter.
26. In System Design process, what is Requirements Determination?
Ans: Requirements determination is the beginning sub phase of analysis. In this sub phase, analysts should gather information on what the system should do from as many sources as possible. There are some traditional methods to help collecting system requirements, such as interviewing, survey, directly observing users, etc.
27. What are the Types of Documentation in System Design? Explain in brief.
ans:
Types of Documentations
When it comes to System Design, there are following four main documentations −
- Program documentation
- System documentation
- Operations documentation
- User documentation
Program Documentation
It describes inputs, outputs, and processing logic for all the program modules.
The program documentation process starts in the system analysis phase and continues during implementation.
This documentation guides programmers, who construct modules that are well supported by internal and external comments and descriptions that can be understood and maintained easily.
Operations Documentation
Operations documentation contains all the information needed for processing and distributing online and printed output. Operations documentation should be clear, concise, and available online if possible.
It includes the following information −
Program, systems analyst, programmer, and system identification.
Scheduling information for printed output, such as report, execution frequency, and deadlines.
Input files, their source, output files, and their destinations.
E-mail and report distribution lists.
Special forms required, including online forms.
Error and informational messages to operators and restart procedures.
Special instructions, such as security requirements.
User Documentation
It includes instructions and information to the users who will interact with the system. For example, user manuals, help guides, and tutorials. User documentation is valuable in training users and for reference purpose. It must be clear, understandable, and readily accessible to users at all levels.
The users, system owners, analysts, and programmers, all put combined efforts to develop a user’s guide.
A user documentation should include −
A system overview that clearly describes all major system features, capabilities, and limitations.
Description of source document content, preparation, processing, and, samples.
Overview of menu and data entry screen options, contents, and processing instructions.
Examples of reports that are produced regularly or available at the user’s request, including samples.
Security and audit trail information.
Explanation of responsibility for specific input, output, or processing requirements.
Procedures for requesting changes and reporting problems.
Examples of exceptions and error situations.
Frequently asked questions (FAQs).
Explanation of how to get help and procedures for updating the user manual.
System Documentation
System documentation serves as the technical specifications for the IS and how the objectives of the IS are accomplished. Users, managers and IS owners need never reference system documentation. System documentation provides the basis for understanding the technical aspects of the IS when modifications are made.
It describes each program within the IS and the entire IS itself.
It describes the system’s functions, the way they are implemented, each program's purpose within the entire IS with respect to the order of execution, information passed to and from programs, and overall system flow.
It includes data dictionary entries, data flow diagrams, object models, screen layouts, source documents, and the systems request that initiated the project.
Most of the system documentation is prepared during the system analysis and system design phases.
During systems implementation, an analyst must review system documentation to verify that it is complete, accurate, and up-to-date, and including any changes made during the implementation process.
28.
If an information system were to be designed for
a retail grocery store/online e-commerce website, what would be the strategic,
tactical, statutory and operational information?
Ans:
By analyzing data collected from different sources, IS can provide valuable information such as which items to launch in which location; so that the company can have advantage over their competitors using this information. IS can also help business houses; in carrying out their business processes differently than their competitors.
Operational Level:
IS promises Operational excellence: In order to achieve higher profitability, businesses improve their operations’ efficiency. Managers make use of IS in business operations to achieve higher levels of productivity and efficiency. An excellent example is the use of the RetailLink system at Wal-Mart; this system digitally links every one of the Wal-Mart’s stores with its suppliers; the supplier is monitoring the items and as soon as an item is purchased, the supplier knows that a replacement must be shipped to the shelf.
IS helps create new products, business models and services: In firms, Information system is a crucial tool in creating new services and products and new business models. Business models describe how the companies produce, deliver and sells a product or service to be successful. An example is Apple Inc; it transformed an old business model which was based on its iPod technology platform that included iPod, iPhone and the iTunes music service.
IS helps monitor & increase Supplier/Customer intimacy: When a customer is served well by a business, he usually responds by returning and purchasing more from the business; this raises the profits and revenues of the business. The more the business engages its suppliers, the better the suppliers are able to provide vital inputs; which in turn lowers costs. An example is the high-end hotel, Manhattan’s ‘The Mandarin Oriental’ and other such high-end hotels; they illustrate the use of IS and technology to achieve better customer intimacy. They track guests’ preferences using computers, such as their preferred television programs, check-in times and room temperatures.
Tactical Level:
IS helps making better decisions: Many managers operate in an information bank and they never have the relevant information at the right moment to make a learned decision; poor outcomes like these loose customers and raise costs. Managers can use real time data while making decisions; IS allow managers to use real-time data from the marketplace while making decisions. An example is the Verizon Corporation, which uses a Web-based digital dashboard that gives managers accurate real-time information on customer complains and network performances. By using this information, managers can rapidly inform customers of the repair work, assign repair resources to the involved areas, and restore service promptly.
Competitive advantage: When the firms achieve the business objectives, for example, customer intimacy, operational excellence, improved decision making, new services, products and business models, than it is most like that they have achieved a competitive advantage already. Accomplishing these things finer than their objects, responding to suppliers and customers in real time, charging less for premium products all add up to higher sales and profits. An example is the Toyota Production System which mainly focuses on organizing work to make continuous improvements, eliminating waste; Toyota Production System is based on what the customers actually ordered.
How are Information Systems transforming the functional areas of organizations?
Computers are used for almost any task. We check email with it, watch media, bank and more. Information is the life of organization, damaged or lost data can cause financial loss, law suits, etc. Information system contains hardware, software, data, applications, communication and people. It helps an organization to manage and secure its critical corporate, customer and employee data. Information system improves work process and gives lot of other benefits. An example is the Transaction Processing System (TPS) which is used in one functional area of a business; it process routine transactions more accurately and efficiently. TPS has many sub-species which are directly linked to their respective functional areas, for example, there is Finance and Accounting Systems for the functional areas of accounts and finance, Human Resource System for the Human Resource area, etc.
29. Define deterministic and probabilistic system with example.
ans:
If given enough information about the deterministic system, an observer could predict all future outcomes with absolute precision. Regardless of how much information you have about a stochastic(*see note below) system, there will always be some randomness in the outcomes.
I think what you really mean to ask is the difference between deterministic and stochastic systems. This distinction may seem nit-picky, but it’s actually pretty important to understand, especially as you get into Bayesian statistics. Probability theory provides a framework for understanding stochastic systems, as well as deterministic systems with limited information. In a pragmatic sense, the age-old question of whether we live in a deterministic or a stochastic world is moot, because the amount of available information means that we need to reason about the world probabilistically regardless.
If you’re interested I’d read about chaotic systems, which seem to break the standard intuition about determinism and stochasticity. These systems are deterministic in the sense that future states can be entirely determined from perfect information, but even the smallest amount of uncertainty cascades into seemingly stochastic behavior. Very cool stuff.
30. What are the major threats to system security? Write down the guidelines to control the access.
Ans:
In Information Security threats can be many like Software attacks, theft of intellectual property, identity theft, theft of equipment or information, sabotage, and information extortion.
Threat can be anything that can take advantage of a vulnerability to breach security and negatively alter, erase, harm object or objects of interest.
Software attacks means attack by Viruses, Worms, Trojan Horses etc. Many users believe that malware, virus, worms, bots are all same things. But they are not same, only similarity is that they all are malicious software that behave differently.
Malware is a combination of 2 terms- Malicious and Software. So Malware basically means malicious software that can be an intrusive program code or a anything that is designed to perform malicious operations on system. Malware can be divided in 2 categories:
- Infection Methods
- Malware Actions
Malware on the basis of Infection Method are following:
- Virus – They have the ability to replicate themselves by hooking them to the program on the host computer like songs, videos etc and then they travel all over the Internet. Ther Creeper Virus was first detected on ARPANET. Examples include File Virus, Macro Virus, Boot Sector Virus, Stealth Virus etc.
- Worms – Worms are also self replicating in nature but they don’t hook themselves to the program on host computer. Biggest difference between virus and worms is that worms are network aware. They can easily travel from one computer to another if network is available and on the target machine they will not do much harm, they will for example consume hard disk space thus slowing down the computer.
- Trojan – The Concept of Trojan is completely different from the viruses and worms. The name Trojan derived from the ‘Trojan Horse’ tale in Greek mythology, which explains how the Greeks were able to enter the fortified city of Troy by hiding their soldiers in a big wooden horse given to the Trojans as a gift. The Trojans were very fond of horses and trusted the gift blindly. In the night, the soldiers emerged and attacked the city from the inside.
Their purpose is to conceal themselves inside the software that seem legitimate and when that software is executed they will do their task of either stealing information or any other purpose for which they are designed.
They often provide backdoor gateway for malicious programs or malevolent users to enter your system and steal your valuable data without your knowledge and permission. Examples include FTP Trojans, Proxy Trojans, Remote Access Trojans etc. - Bots –: can be seen as advanced form of worms. They are automated processes that are designed to interact over the internet without the need of human interaction. They can be good or bad. Malicious bot can infect one host and after infecting will create connection to the central server which will provide commands to all infected hosts attached to that network called Botnet.
31. What are the differences between initial investigation and feasibility study in system development life cycle? How can you relate them?
Ans : likely depends on who you ask but an initial investigation feasibility study is often an early step of some SDLCs. Not all System Development Life Cycles are the same. Just as not all Software Development Life Cycles are the same. But, any business effort should not be taken seriously until some initial investigation of the feasibility and of the ROI (return on investment) are done.
32. “Fact Gathering” is a role of system analyst. Explain.
Ans:
For an Analyst Data and fact gathering is important step, on which he/she can develop better understanding of existing system and its problems, based on this analyst can understand the requirements of new system.
There are various techniques to gather data and facts of system. some of them re as follows :
- Record view and Background reading
- Interviews
- Questionnaires
- Group communication
- Presentation
- Site visiting
- Observation
- Record view and Background reading : Information related to system and organization is already available in some type documents and records(like system user manual , system review/audit, brochures etc. ) or is published in the sources like newspapers, magazines, journals etc. Study of already available document is the fastest and independant way of gathering fact and information based on which analyst can prepare questions for further gathering exercise.
- Interviews : This method is used to collect the information from groups or individuals. Analyst selects the people who are related with the system for the interview. In this method the analyst sits face to face with the people and records their responses by which analyst learn about the existing system, its problem and expectation with the system. The interviewer must plan in advance the type of questions he/ she is going to ask and should be ready to answer any type of question.
The information collected is quite accurate and reliable as the interviewer can clear and cross check the doubts there itself. This method also helps gap the areas of misunderstandings and help to discuss about the future problems. - Questionnaires : This method seeks information from the person in written and prescribed format. This is a quickest way for gathering information if respondents are scattered geographically or there is no time for the interviews. Questions can be : structured or unstructured. structured question where the answers are in the form of YES/NO , multiple choice option selection , ratings, fill int hte blanks. unstructured questions where person is asked for his opinion and he/she can answer it freely.
- Group Communication : This method is often used when there no time for personal interview and information is required from face to face sessions. As there are many person present many type of ideas can be heard. Scheduling such sessions is a skillful matter because it has many problems such as : discussion may be dominated by one person others may shy to respond, presence of seniors in the group may not allow others to present their views freely, discussion may lead to verbal fight etc.
- Presentation : Sometime presentation can also be conducted by analyst for presenting his understanding for the system and problems with it. Such presentation may include showing slide , interacting with people and talking to them regarding system, asking questions, answering questions etc. Presentations are useful when users are passive or too busy to actively explain things.
- Site Visiting : it is the process of examining the problems which had previously solved by other sources that can be either human or documents. To solve the requirements of problem, the analyst visits to other organization that had previously experienced for similar problems. In addition, the analyst can also find the information from database, reference books, case studies and Internet
- Observation : Another fact finding technique is observation. In this technique, system analyst participates in the organization, studies the flow of documents, applies the existing system, and interacts with the users. Observation can be a useful technique when the system analyst have user point of view. Sampling technique called work sampling is useful for observation. By using this technique, system analyst can know how employees spend their days.
33. What is technical, economic and operational feasibility?
ANs: TECHNICAL FEASIBILITY
A large part of determining resources has to do with assessing technical feasibility. It considers the technical requirements of the proposed project. The technical requirements are then compared to the technical capability of the organization. The systems project is considered technically feasible if the internal technical capability is sufficient to support the project requirements.
The analyst must find out whether current technical resources can be upgraded or added to in a manner that fulfills the request under consideration. This is where the expertise of system analysts is beneficial, since using their own experience and their contact with vendors they will be able to answer the question of technical feasibility.
The essential questions that help in testing the operational feasibility of a system include the following:
OPERATIONAL FEASIBILITY
Operational feasibility is dependent on human resources available for the project and involves projecting whether the system will be used if it is developed and implemented.
Operational feasibility is a measure of how well a proposed system solves the problems, and takes advantage of the opportunities identified during scope definition and how it satisfies the requirements identified in the requirements analysis phase of system development.Operational feasibility reviews the willingness of the organization to support the proposed system. This is probably the most difficult of the feasibilities to gauge. In order to determine this feasibility, it is important to understand the management commitment to the proposed project. If the request was initiated by management, it is likely that there is management support and the system will be accepted and used. However, it is also important that the employee base will be accepting of the change.
The essential questions that help in testing the operational feasibility of a system include the following:
ECONOMIC FEASIBILITY
Economic analysis could also be referred to as cost/benefit analysis. It is the most frequently used method for evaluating the effectiveness of a new system. In economic analysis the procedure is to determine the benefits and savings that are expected from a candidate system and compare them with costs. If benefits outweigh costs, then the decision is made to design and implement the system. An entrepreneur must accurately weigh the cost versus benefits before taking an action.Possible questions raised in economic analysis are:
The concerned business must be able to see the value of the investment it is pondering before committing to an entire system study. If short-term costs are not overshadowed by long-term gains or produce no immediate reduction in operating costs, then the system is not economically feasible, and the project should not proceed any further. If the expected benefits equal or exceed costs, the system can be judged to be economically feasible. Economic analysis is used for evaluating the effectiveness of the proposed system.
The economical feasibility will review the expected costs to see if they are in-line with the projected budget or if the project has an acceptable return on investment. At this point, the projected costs will only be a rough estimate. The exact costs are not required to determine economic feasibility. It is only required to determine if it is feasible that the project costs will fall within the target budget or return on investment. A rough estimate of the project schedule is required to determine if it would be feasible to complete the systems project within a required timeframe. The required timeframe would need to be set by the organization.
34. Write down the steps in feasibility analysis.
ans:
- Conduct a Preliminary Analysis. Begin by outlining your plan. ...
- Prepare a Projected Income Statement. ...
- Conduct a Market Survey, or Perform Market Research. ...
- Plan Business Organization and Operations. ...
- Prepare an Opening Day Balance Sheet. ...
- Review and Analyze All Data. ...
- Make a Go/No-Go Decision.
35. Explain with an example of each variety of closed question:
ans: A closed-ended question refers to any question for which a researcher provides research participants with options from which to choose a response. ... Examples of close-ended questions which may elicit a "yes" or "no" response include: Were you born in 2020?
a. Ranking scale question
b. Fill in the blanks question
c. Dichotomous questions
36. What categories of information are relevant to decision making in business. Relate each category to the managerial level and information system.
ans:
MAJOR TYPES OF SYSTEMS IN ORGANIZATIONS
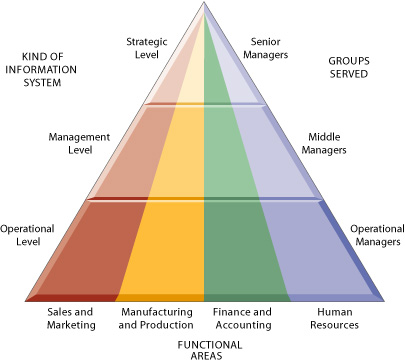
Because there are different interests, specialties, and levels in an organization, there are different kinds of systems. No single system can provide all the information an organization needs. Figure 2-1 illustrates one way to depict the kinds of systems found in an organization. In the illustration, the organization is divided into strategic, management, and operational levels and then is further divided into functional areas, such as sales and marketing, manufacturing and production, finance and accounting, and human resources. Systems are built to serve these different organizational interests (Anthony, 1965).
 |
37. Give example of informal and formal system and also explain why they are called so?
ans:
FORMAL COMMUNICATION NETWORKS - DEFINITION
A single chain network exists between a superior and his subordinate
In a wheel network all subordinates under one superior communicate through him only as he acts as a hub of the wheel.
In a circle network each person can communicate with the two beside him.
In a free flow network there is no restriction in communication.
In an inverted V network the subordinate can talk to his superior as well as his subordinates.
INFORMAL COMMUNICATION AND GRAPEVINE NETWORK - DEFINITION
Informal communication is the communication that takes place outside the formal line of communication.
The Grapevine network is a informal communication network.
In a grapevine network, each person can communicate with the other in a single strand network.
38. What additional information would you like to gather a second interview?
ans: During a second interview, you will also be asked more specific interview questions about the job, the company, your ability to perform in the role, and how your skills and abilities translate into what the company is seeking in the candidate they are going to hire.
39. A system analyst should be an "Analytical Mind", explain it.
ans:
Working as a systems analyst means you're assessing the efficiency and effectiveness of an organization's IT system. When working in this position, it's also your responsibility to develop plans for improving any shortcomings in the efficiencies you find. Under most circumstances, those working as a systems analyst hold either a bachelor's or master's degree in computer engineering or computer science.
Table of Contents
- Systems Analyst Job Description Sample
- Systems Analyst Salary
- Systems Analyst Job Description For Resume
- Systems Analyst Skills
- Systems Analyst Duties & Responsibilities
- Systems Analyst Requirements
40. What are malware? Distinguish between DOS and DDOS attacks of a server? How to recover from those attacks?
ans: The only difference between them is their scale. Single DoS attacks come from one source, while DDoS (distributed) attacks come from multiple locations, often spoofed. ... DoS attacks are on the lower end of that spectrum while DDoS attacks are on the higher end
41. Briefly describe physical security and data security with example.
ans: Physical security involves the use of multiple layers of interdependent systems that can include CCTV surveillance, security guards, protective barriers, locks, access control, perimeter intrusion detection, deterrent systems, fire protection, and other systems designed to protect persons and property.
42. What are computer crimes? Briefly explain at least three example of computer crimes happened in Bangladesh.
ans:
- Improperly accessing a computer, system, or network;
- Modifying, damaging, using, disclosing, copying, or taking programs or data;
- Introducing a virus or other contaminant into a computer system;
- Using a computer in a scheme to defraud;
- Interfering with someone else's computer access or use;
43. What are the differences between open ended questionnaire and close ended questionnaire regarding information gathering tool?
ans: Open-ended questions are questions that allow someone to give a free-form answer. Closed-ended questions can be answered with “Yes” or “No,” or they have a limited set of possible answers (such as: A, B, C, or All of the Above)
44. What are the steps an analyst should follow to design an information system? Explain with diagram.
ans:
Systems Design
It is a process of planning a new business system or replacing an existing system by defining its components or modules to satisfy the specific requirements. Before planning, you need to understand the old system thoroughly and determine how computers can best be used in order to operate efficiently.
System Design focuses on how to accomplish the objective of the system.
System Analysis and Design (SAD) mainly focuses on −
- Systems
- Processes
- Technology
What is a System?
The word System is derived from Greek word Systema, which means an organized relationship between any set of components to achieve some common cause or objective.
A system is “an orderly grouping of interdependent components linked together according to a plan to achieve a specific goal.”
Constraints of a System
A system must have three basic constraints −
A system must have some structure and behavior which is designed to achieve a predefined objective.
Interconnectivity and interdependence must exist among the system components.
The objectives of the organization have a higher priority than the objectives of its subsystems.
For example, traffic management system, payroll system, automatic library system, human resources information system.
Properties of a System
A system has the following properties −
Organization
Organization implies structure and order. It is the arrangement of components that helps to achieve predetermined objectives.
Interaction
It is defined by the manner in which the components operate with each other.
For example, in an organization, purchasing department must interact with production department and payroll with personnel department.
Interdependence
Interdependence means how the components of a system depend on one another. For proper functioning, the components are coordinated and linked together according to a specified plan. The output of one subsystem is the required by other subsystem as input.
Integration
Integration is concerned with how a system components are connected together. It means that the parts of the system work together within the system even if each part performs a unique function.
Central Objective
The objective of system must be central. It may be real or stated. It is not uncommon for an organization to state an objective and operate to achieve another.
The users must know the main objective of a computer application early in the analysis for a successful design and conversion.
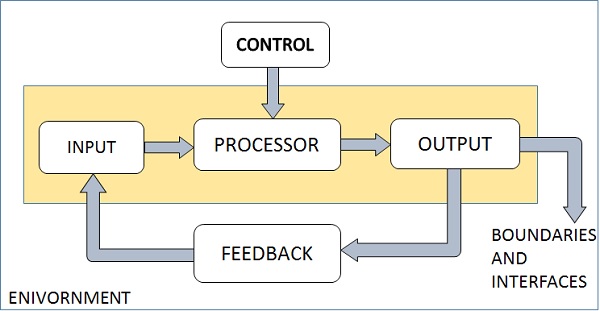
Elements of a System
The following diagram shows the elements of a system −
45. What is data dictionary? Why it is important regarding software project management?
ans:
46. What is information gathering? How we gather information to analysis a system?Which of the following methods would you use and why?
ans: the requirements of a system, information must be gathered from the customer. Ideally, the information obtained will enable a well defined, accurate, and complete ... There are many techniques that can be employed when gathering information. ... providing the information, will determine which techniques you should use
47. Elaborate on the steps taken in system testing that lead to the user's acceptance of the system.
ans: Acceptance tests are black-box system tests. Users of the system perform tests in line with what would occur in real-time scenarios and verify whether or not the software/application meets all specifications. The requirement for acceptance testing should be cleared at the early stages of product development.
48. What is encryption? How does it work? What type of system would appropriate for this technology? Illustrate.
ans: Our definition will cover how encryption works, and how you can use it to ... role in securing many different types of information technology (IT) assets. ... There are three major components to any encryption system: the ... Meanwhile, NIST has encouraged the creation of cryptographic algorithms suitable
49. Distinguish between software maintenance and enhancement.
ans: Maintenance: To resolve day to day issues that come in the application by tweaking the source code. Enhancement: To add new features to the software as new requirements or Process improvement iniitatives.
50. Talk to a book shop owner and find out what his information requirements are. Divide it into operational, tactical, strategic and statutory components. Describe how his operational and tactical information needs could be satisfied if he installs a PC.
ans: Managers use tactical planning to outline what the various parts of the organization must do for the organization to be successful at some point one year or less into the future. ... Operational planning is the process of linking strategic goals and objectives to tactical goals and objectives.
51.
Specify the purpose of the system testing. What
performance criteria are used for system
testing? Discuss.
ans: Performance Testing is a type of software testing that is carried out to test the speed, scalability, stability and reliability of the software product or application.
52.
List five of the several measures an analyst can
take to improve the security, privacy, and
confidentiality of data, systems, networks, individuals, and organizations that
use ecommerce web applications.
ans: Whether You Know It or Not, You Make Choices about What and How You Share Each Day. Follow These 6 Steps to Improve Your Privacy. Small Actions Can Make a Big Difference. Internet Leadership. Internet Policy. Tools & Training. Internet Privacy.
53.
|
5. |
ans:
Disintermediation is the removal of the third party that offers intermediation services between two trading parties in a supply chain. It is basically “cutting out the middle man” from the distribution channel allowing direct links between buyers and sellers. Businesses/consumers would not have to go traditional distribution channels, which had some type of intermediate; this includes distributor, wholesaler, brokers, or agent etc. With disintermediation, companies are able to deal with every customer directly, for example via the Internet.
An example of supply chain disintermediation is a manufacturer selling directly to retailers, rather than indirectly through wholesalers. A familiar example of disintermediation is Dell, Inc. Dell sells many of its systems direct to the consumer bypassing traditional retail chains. Dell - has succeeded in creating a brand, well recognized by consumers, profitable and with continuous growth. Likewise, maybe the most notable example to reintermediation is the Levi Strauss company, who unsuccessfully launched a multimillion dollar web site and later shut down most of its online operations.
The advantage of disintermediation is obviously the greater efficiency and lower cost achieved by reducing the number of transactions and processes involved.
Disintermediation can help producers in many ways this is because they are able to save money as organisation do need to pay the intermediation.
The term ‘disintermediation’ has been offered to describe the alleged move towards shorter value chains in electronic marketplaces.
Producers can benefit from increasing their profit margins and passing a part of their savings to the consumers who thus enjoy lower prices and greater choice. Further, where one producer can dominate on price or quality, direct sales reduces the uncertainty of consumers and a “winner take all” market can emerge. Consumers are able to get their products straight away with low cost as it does not have to go through the ‘middle man’ where they have to pay and make deals at low prices. This can attract more customers as businesses are able to sell at low prices which catch more attention making more customer awareness and able to retain existing customers. ASOS is based online so the advent of e-commerce made it possible for them to sell directly to customers. So they do not have to pay intermediation which let them make more profits and as they save money they are able to use it on their customers by providing a better service, more variety of products, more advanced promoting etc.
54. What are the unique features of electronic commerce (e-commerce), digital markets, and digital goods?
ans: Unique features of e-commerce technology include ubiquity, global reach, universal technology standards, richness, interactivity, information density, capabilities for personalization and customization, and social technology.
55. What is the difference between quantitative data and qualitative data? In what situations could the number 10 be considered qualitative data?
ans : Quantitative data can be counted, measured, and expressed using numbers. Qualitative data is descriptive and conceptual. Qualitative data can be categorized based on traits and characteristics. Now that we got the differences out of the way, let's dive into each type of data using real-world
56. We all interact with various information systems every day: at the grocery store, at work, at university, even in our cars (at least some of us).
ans : Information system, an integrated set of components for collecting, storing, and processing data and for providing information, knowledge, and digital products. Business firms and other organizations rely on information systems to carry out and manage their operations, interact with their customers and suppliers, and compete in the marketplace. Information systems are used to run interorganizational supply chains and electronic markets. For instance, corporations use information systems to process financial accounts, to manage their human resources, and to reach their potential customers with online promotions. Many major companies are built entirely around information systems. These include eBay, a largely auction marketplace; Amazon, an expanding electronic mall and provider of cloud computing services; Alibaba, a business-to-business e-marketplace; and Google, a search engine company that derives most of its revenue from keyword advertising on Internet searches. Governments deploy information systems to provide services cost-effectively to citizens. Digital goods—such as electronic books, video products, and software—and online services, such as gaming and social networking, are delivered with information systems. Individuals rely on information systems, generally Internet-based, for conducting much of their personal lives: for socializing, study, shopping, banking, and entertainment.
Write down the four different information systems you interact with every day. See if you can identify the technologies, people, and processes involved in making these systems work.
ans:
Almost all programs in business require students to take a course in something called information systems. But what exactly does that term mean? Let’s take a look at some of the more popular definitions, first from Wikipedia and then from a couple of textbooks:
- “Information systems (IS) is the study of complementary networks of hardware and software that people and organizations use to collect, filter, process, create, and distribute data.”[1]
- “Information systems are combinations of hardware, software, and telecommunications networks that people build and use to collect, create, and distribute useful data, typically in organizational settings.”[2]
- “Information systems are interrelated components working together to collect, process, store, and disseminate information to support decision making, coordination, control, analysis, and viualization in an organization.”[3]
As you can see, these definitions focus on two different ways of describing information systems: the components that make up an information system and the role that those components play in an organization. Let’s take a look at each of these.
THE COMPONENTS OF INFORMATION SYSTEMS
As I stated earlier, I spend the first day of my information systems class discussing exactly what the term means. Many students understand that an information system has something to do with databases or spreadsheets. Others mention computers and e-commerce. And they are all right, at least in part: information systems are made up of different components that work together to provide value to an organization.
The first way I describe information systems to students is to tell them that they are made up of five components: hardware, software, data, people, and process. The first three, fitting under the technology category, are generally what most students think of when asked to define information systems. But the last two, people and process, are really what separate the idea of information systems from more technical fields, such as computer science. In order to fully understand information systems, students must understand how all of these components work together to bring value to an organization.
TECHNOLOGY
Technology can be thought of as the application of scientific knowledge for practical purposes. From the invention of the wheel to the harnessing of electricity for artificial lighting, technology is a part of our lives in so many ways that we tend to take it for granted. As discussed before, the first three components of information systems – hardware, software, and data – all fall under the category of technology. Each of these will get its own chapter and a much lengthier discussion, but we will take a moment here to introduce them so we can get a full understanding of what an information system is.
Hardware
Information systems hardware is the part of an information system you can touch – the physical components of the technology. Computers, keyboards, disk drives, iPads, and flash drives are all examples of information systems hardware. We will spend some time going over these components and how they all work together in chapter 2.
Software
 https://s3-us-west-2.amazonaws.com/courses-images/wp-content/uploads/sites/1451/2017/01/26004901/hwswappuser-300x255-65x55.png 65w, https://s3-us-west-2.amazonaws.com/courses-images/wp-content/uploads/sites/1451/2017/01/26004901/hwswappuser-300x255-225x191.png 225w" sizes="(max-width: 300px) 100vw, 300px">Software is a set of instructions that tells the hardware what to do. Software is not tangible – it cannot be touched. When programmers create software programs, what they are really doing is simply typing out lists of instructions that tell the hardware what to do. There are several categories of software, with the two main categories being operating-system software, which makes the hardware usable, and application software, which does something useful. Examples of operating systems include Microsoft Windows on a personal computer and Google’s Android on a mobile phone. Examples of application software are Microsoft Excel and Angry Birds. Software will be explored more thoroughly in chapter 3.
https://s3-us-west-2.amazonaws.com/courses-images/wp-content/uploads/sites/1451/2017/01/26004901/hwswappuser-300x255-65x55.png 65w, https://s3-us-west-2.amazonaws.com/courses-images/wp-content/uploads/sites/1451/2017/01/26004901/hwswappuser-300x255-225x191.png 225w" sizes="(max-width: 300px) 100vw, 300px">Software is a set of instructions that tells the hardware what to do. Software is not tangible – it cannot be touched. When programmers create software programs, what they are really doing is simply typing out lists of instructions that tell the hardware what to do. There are several categories of software, with the two main categories being operating-system software, which makes the hardware usable, and application software, which does something useful. Examples of operating systems include Microsoft Windows on a personal computer and Google’s Android on a mobile phone. Examples of application software are Microsoft Excel and Angry Birds. Software will be explored more thoroughly in chapter 3.
Data
The third component is data. You can think of data as a collection of facts. For example, your street address, the city you live in, and your phone number are all pieces of data. Like software, data is also intangible. By themselves, pieces of data are not really very useful. But aggregated, indexed, and organized together into a database, data can become a powerful tool for businesses. In fact, all of the definitions presented at the beginning of this chapter focused on how information systems manage data. Organizations collect all kinds of data and use it to make decisions. These decisions can then be analyzed as to their effectiveness and the organization can be improved. Chapter 4 will focus on data and databases, and their uses in organizations.
Networking Communication: A Fourth Technology Piece?
Besides the components of hardware, software, and data, which have long been considered the core technology of information systems, it has been suggested that one other component should be added: communication. An information system can exist without the ability to communicate – the first personal computers were stand-alone machines that did not access the Internet. However, in today’s hyper-connected world, it is an extremely rare computer that does not connect to another device or to a network. Technically, the networking communication component is made up of hardware and software, but it is such a core feature of today’s information systems that it has become its own category. We will be covering networking in chapter 5.
PEOPLE
ing about information systems, it is easy to get focused on the technology components and forget that we must look beyond these tools to fully understand how they integrate into an organization. A focus on the people involved in information systems is the next step. From the front-line help-desk workers, to systems analysts, to programmers, all the way up to the chief information officer (CIO), the people involved with information systems are an essential element that must not be overlooked. The people component will be covered in chapter 9.
PROCESS
The last component of information systems is process. A process is a series of steps undertaken to achieve a desired outcome or goal. Information systems are becoming more and more integrated with organizational processes, bringing more productivity and better control to those processes. But simply automating activities using technology is not enough – businesses looking to effectively utilize information systems do more. Using technology to manage and improve processes, both within a company and externally with suppliers and customers, is the ultimate goal. Technology buzzwords such as “business process reengineering,” “business process management,” and “enterprise resource planning” all have to do with the continued improvement of these business procedures and the integration of technology with them. Businesses hoping to gain an advantage over their competitors are highly focused on this component of information systems.
 Building Matrix Reports (Salesforce Classic)
Building Matrix Reports (Salesforce Classic)