Basic Information:
Course Code: CSE 423
Course Title: Information Security
Program: B.Sc in Computer Science and Engineering
Faculty: Science and Information Technology
Semester: Fall; Year: 2022
Credit: 3.0; Contact Hour: 2 Hours/ Week
Course Category: Core Engineering
Course Instructor:
Lamia Rukhsara
Lecturer
Office: Room #705, AB4 Building, Daffodil
Smart City
Cell Number# +880 1819652162
Email: lamia.cse@diu.edu.bd
Counselling Hour: Sunday-Wednesday (10:00AM -4:00 PM)
Course
Rationale:
Information security — or infosec — is the protection of information by people and organizations in order to keep information safe for themselves, their company, and their clients. Every organization needs protection against cyber-attacks and security threats. Cybercrime and malware are constant threats to anyone with an Internet presence, and data breaches are time-consuming and expensive. The goal of IT security is to protect these assets, devices and services from being disrupted, stolen or exploited by unauthorized users, otherwise known as threat actors.
Course
Objectives:
To provide a solid
conceptual understanding of the fundamentals of Information Security. More specifically,
-To
learn basics of information security, in both management aspect and technical
aspect.
-To
learn various types of security threats and attacks
-To
learn basics of Security risks and Management process
-To
learn ways to manage, detect and response to incidents and attacks.
-To
learn the benefits of AI and ML in the field of Information Security
-To
learn basics of application of cryptography which are one of the key technology
to implement security functions.
-To
learn the Legal and Ethical issues in information security
Course Learning Outcomes (CLO's):
|
CLO1
|
Interpret the components, tools
and techniques of Information Security systems
|
|
CLO2
|
Analyze various Information
security threats, risks and propose controls for it.
|
|
CLO3
|
Explain the Ethical issues and
Laws in the field of Information Security
|
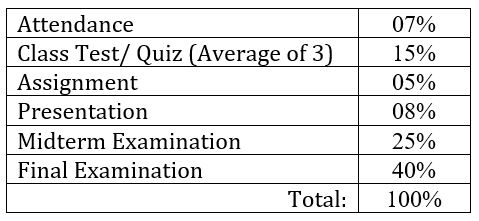
Assessment Strategies: